What Is PPTP (Point-to-Point Tunneling Protocol)?
PPTP (Point-to-Point Tunneling Protocol) is a network protocol used to establish a secure VPN connection over the internet.
Point-to-Point Tunneling Protocol facilitates the private transfer of data from a remote client to a server by encapsulating packets at a TCP/IP level. Despite its role in early VPN development, PPTP has been largely superseded by more secure protocols because of its known vulnerabilities and weak encryption standards.
How Does PPTP Work?
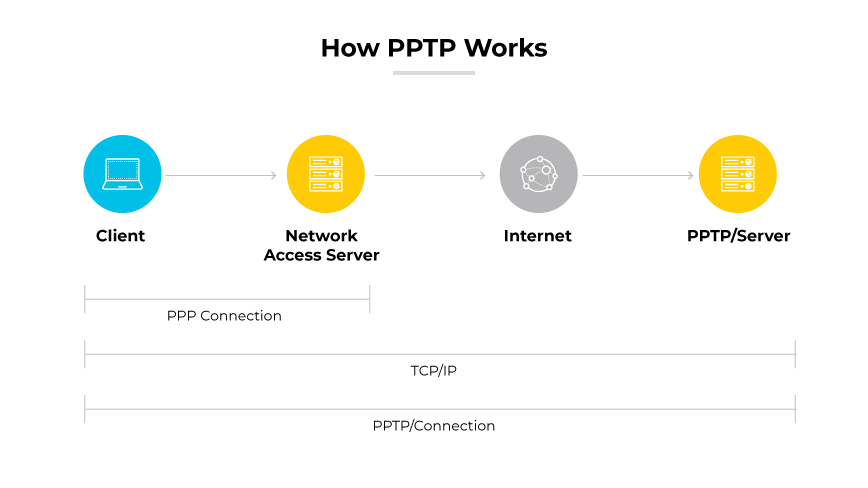
Point-to-Point Tunneling Protocol (PPTP) establishes VPN connections by encapsulating (PPP) frames in IP packets for transmission over the internet. It operates by using a TCP control channel and a Generic Routing Encapsulation (GRE) tunnel. This combination allows the protocol to encapsulate PPP packets, which makes it possible to use VPNs over diverse networks.
The protocol uses a client server architecture, where the client initiates a connection to the server to establish the tunnel. The protocol utilizes TCP port 1723 for setting up the control channel and GRE for tunneling the PPP frames. This dual component structure facilitates the management of VPN sessions and the transmission of data packets securely between client and server.
Within the protocol operation, two VPN tunneling modes exist: voluntary and compulsory. Voluntary tunneling is initiated by the client and occurs after the network connection has been made. Compulsory tunneling is initiated by the server, typically at the internet service provider (ISP) level. These modes determine the initiation point and control of the tunneling process.
Although PPTP Tunneling Protocol was a groundbreaking technology for its time, its security limitations have been highlighted with the advent of more advanced protocols.
Why Is PPTP Obsolete?
Point-to-Point Tunneling Protocol has become obsolete in the enterprise security world due to significant security concerns. Initially embraced for its simplicity and speed, the protocol fell out of favor as vulnerabilities became apparent. Point-to-Point Tunneling Protocol relies on the MS-CHAP (Challenge Handshake Authentication Protocol) v1/v2 authentication protocols, which are now considered weak against modern cryptographic attacks. The encryption method it uses, MPPE (Microsoft Point-to-Point Encryption), only offers up to 128-bit keys which have been deemed insufficient for protecting against advanced threats.
Enterprises have shifted towards more secure protocols due to Point-to-Point Tunneling Protocol’s inability to offer robust protection in the evolving landscape of cyber threats. The protocol's structure is susceptible to several types of attacks, including the well-documented bit-flipping attacks. Such vulnerabilities could potentially allow attackers to decrypt data streams or impersonate authorized users. Limited compatibility with NAT firewalls contributes to its obsolescence, as it does not support modern network configurations well.
The move away from this protocol in favor of more secure VPN solutions reflects the ongoing advancement in cybersecurity measures. As businesses prioritize protecting data and systems, adoption of protocols with stronger authentication methods and more sophisticated encryption has become critical. Protocols like OpenVPN, L2TP/IPsec, and newer innovations like SASE offer a more reliable security posture for remote access. These cybersecurity advancements have made Point-to-Point Tunneling Protocol a relic of the past in enterprise VPN strategies.
PPTP Pros and Cons
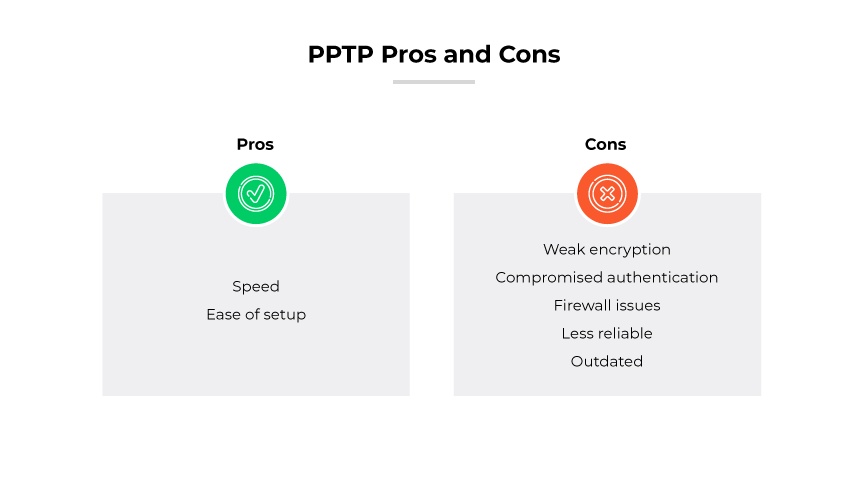
While outdated, the Point-to-Point Tunneling Protocol has certain aspects that made it popular in the past. Its main advantages were speed and ease of setup. PPTP is fast because it uses less complex encryption processes. This also makes it very easy to implement across different operating systems. These factors once contributed to its widespread adoption in the enterprise sector.
PPTP's simplicity is also its Achilles' heel when it comes to security. The protocol uses weak encryption standards, which are susceptible to numerous cyber threats. Additionally, its authentication methods, particularly the MS-CHAP v1/v2, are compromised and no longer provide secure user verification. The protocol struggles with modern firewall restrictions, often leading to connectivity issues. These factors make it an unreliable and unsuitable option for modern enterprises.
What Is PPTP Passthrough?
PPTP Passthrough is a router feature that allows Point-to-Point Tunneling Protocol traffic to be routed through a Network Address Translation (NAT) device. PPTP does not inherently support NAT, which is commonly used to share a single IP address among multiple devices on a local network. With Passthrough enabled, the router permits the PPTP connections from devices within the internal network to establish a tunnel to a remote PPTP server.
The mechanism modifies the traffic in such a way that the NAT device can distinguish and manage multiple VPN connections from the same network. This is relevant in an enterprise setting where several remote users may need to connect to the company’s network through Point-to-Point Tunneling Protocol. Although Passthrough helps in overcoming the limitations of older protocols and routers, modern VPN protocols have made this feature less critical. Modern protocols have built-in support for NAT and offer superior security and compatibility.
Comparing PPTP with Other Protocols
PPTP vs. OpenVPN
Point-to-Point Tunneling Protocol falls short when compared to OpenVPN, which boasts strong AES-256 encryption. Being open source, OpenVPN is continuously audited and updated, ensuring robust security measures. While PPTP may offer faster speeds due to simpler encryption, OpenVPN provides a more secure and stable connection.
PPTP vs. IKEv2
IKEv2 can quickly reestablish lost connections, making it ideal for mobile users who switch between network types. Although PPTP might be faster, IKEv2 offers more reliable security protocols and encryption standards, such as AES-256.
PPTP vs. L2TP
L2TP is often paired with IPsec to provide better security features than PPTP can offer on its own. While both protocols can be easy to set up, L2TP/IPsec provides stronger encryption, which can impact speed but offers significantly enhanced security. This is a trade-off many enterprises find worthwhile.
PPTP vs. WireGuard
WireGuard is a newer protocol with a much smaller codebase, which could mean potentially fewer vulnerabilities and higher performance efficiency. It offers comparable speeds to Point-to-Point Tunneling Protocol but with much stronger security protocols. WireGuard's modern encryption techniques and streamlined operation make it a successor to older protocols like PPTP in enterprise environments.
