- What is Security Analytics?
-
What is SIEM?
- SIEM: The Foundation for XSIAM
- How SIEM Works
- Key Functions and Benefits of SIEM
- Role of AI and ML in SIEM
- SIEM Integration
- SIEM Use Cases
- How to Choose a SIEM Solution
- Best Practices for SIEM Implementation
- SIEM vs Other Security Solutions
- What is Cloud SIEM?
- The Evolution of SIEM
- The Future of SIEM
- SIEM FAQs
- What is Security Information and Event Management (SIEM) Integration?
- What is SIEM Logging?
- What is a SIEM Solution in a SOC?
- How Do SIEM Tools Benefit SOC Teams?
-
What Is the Role of AI and ML in Modern SIEM Solutions?
- The Evolution of SIEM Systems
- Benefits of Leveraging AI and ML in SIEM Systems
- SIEM Features and Functionality that Leverage AI and ML
- AI Techniques and ML Algorithms that Support Next-Gen SIEM Solutions
- Predictions for Future Uses of AI and ML in SIEM Solutions
- Role of AI and Machine Learning in SIEM FAQs
-
What is Cloud SIEM?
- Why Use a Cloud SIEM?
- How SIEM Interacts with Cloud Environments and SaaS Applications
- Core Cloud SIEM Features and Capabilities
- Cloud SIEM Deployment Models
- On-Premise vs. Cloud SIEM Deployment
- Key Steps for Implementing Cloud SIEM
- Cloud SIEM Challenges
- Considerations of a Cloud Native SIEM Solution
- Cloud SIEM FAQs
- What Is Security Information Event Management (SIEM) Software?
- What are SIEM Use Cases?
- What Are Security Information and Event Management (SIEM) Tools?
What Is Security Event Management (SEM)?
Security event management (SEM) is the process of monitoring, correlating and managing security events within an organization's IT infrastructure to detect and respond to potential security threats or incidents.
SEM focuses primarily on the management and analysis of security events. It typically involves event monitoring via logs and activities, correlation and analysis, alerting and notification, incident response, and reporting and compliance.
Get the Full Picture | Cortex XSIAM - Palo Alto Networks
Why is SEM Important to IT Security?
SEM is vital as it is the first defense against cyberthreats. It's the difference between catching a cyberattack as it happens and dealing with the aftermath of a breach. SEM's real-time monitoring and alert systems allow swift action, minimizing damage and protecting sensitive data.
The primary goal of SEM is to distinguish normal activities--typical user behaviors, network operations, and system processes--from suspicious or malicious behavior. This process involves correlating event logs and log data using predefined rules, signatures, and algorithms to identify patterns indicative of potential security incidents.
Through real-time monitoring and analysis, SEM enables security teams to swiftly recognize and respond to anomalies that could signify a breach or an impending threat. Further, SEM plays a pivotal role in compliance and regulatory adherence.
Many industries operate within strict regulatory frameworks mandating comprehensive security measures. SEM assists organizations in meeting these requirements by providing comprehensive audit trails, incident response capabilities, and reports for compliance assessments.
How does SEM work?
SEM collects and analyzes log data from various sources within an IT environment. It's like piecing together a puzzle - each piece of data helps form a clearer picture of the network's security status, allowing for quick identification of anomalies or malicious activities.
The SEM process is crucial to an organization's cybersecurity strategy. It involves a series of stages that enable security teams to detect, investigate, and respond to potential security threats promptly and effectively.
Stage One: Data Collection
This involves gathering logs and events from various sources across the network, such as firewalls, intrusion detection systems, and servers. The collected data is then stored in a centralized repository for analysis.
Stage Two: Normalization
Since logs and events can have different formats and structures depending on the source, they need to be converted into a standardized format for unified analysis. This involves mapping the different log fields to a common schema, so they can be easily correlated and analyzed.
Stage Three: Correlation
This involves analyzing the collected data to identify patterns or anomalies indicating security threats. This is typically done using advanced analytics techniques such as machine learning and behavioral analysis, which can help detect complex attack patterns that may go unnoticed by traditional rule-based systems.
Stage Four: Alerting
When a potential security threat is detected, the SEM system generates alerts or notifications for security teams to investigate and respond to. These alerts typically include details on the threat's nature, the incident's severity, and recommended actions for containment and mitigation.
Stage Five: Incident Response
This involves taking appropriate actions to contain, mitigate, and remediate security incidents. This may include isolating affected systems, blocking malicious traffic, restoring backups, and conducting forensic analysis to determine the incident's root cause.
By following these stages, organizations can establish an intense SEM process to proactively detect and respond to security threats, reducing the risk of data breaches and other cyberattacks.
Scenario: Detecting and Mitigating an Insider Threat
Context
Organization Profile: A large healthcare provider with sensitive patient data stored on its network.
IT Infrastructure: A combination of internal servers and cloud-based services, with access controls for different levels of employee clearance.
Pre-Incident Phase
SEM Implementation: The organization utilizes a sophisticated SEM system to monitor and analyze real-time events across its network.
Incident Initiation
Suspicious Activity: A billing department employee who usually accesses a specific set of patient records begins accessing many files unrelated to their usual duties. These files contain sensitive patient information.
SEM Detection
- Real-time Monitoring: The SEM system is configured to flag any unusual access patterns based on predefined rules. It detects abnormal data access behavior from the employee's user account.
- Alert Generation: An alert is automatically triggered and sent to the cybersecurity team, indicating potential unauthorized access or an insider threat.
- Incident Assessment: The cybersecurity team immediately reviews the alert. They assess the access logs and confirm that the employee’s behavior deviates significantly from their normal pattern.
- Employee Verification: The team contacts the employee’s supervisor to verify whether the data access is legitimate or part of an assigned task.
Containment and Investigation
- Account Suspension: Upon confirmation that the access is unauthorized, the employee's account is temporarily suspended to prevent further data access.
- Investigation: The cybersecurity team initiates a thorough investigation, including interviewing the employee, reviewing access logs in detail, and checking for data exfiltration attempts.
Resolution
- Outcome Determination: The investigation reveals that the employee accessed patient data out of curiosity, violating the organization’s privacy policies.
- Action Taken: According to the organization's policies, the employee is subjected to disciplinary action. The incident is documented, and a review of access controls is conducted.
Post-Incident Analysis
- SEM System Update: The SEM rules are updated to finely tune the detection of unusual data access patterns, improving sensitivity to potential insider threats.
- Employee Training: Additional training sessions on data privacy and security protocols are organized for all employees to prevent similar incidents.
How SIEM Software Works
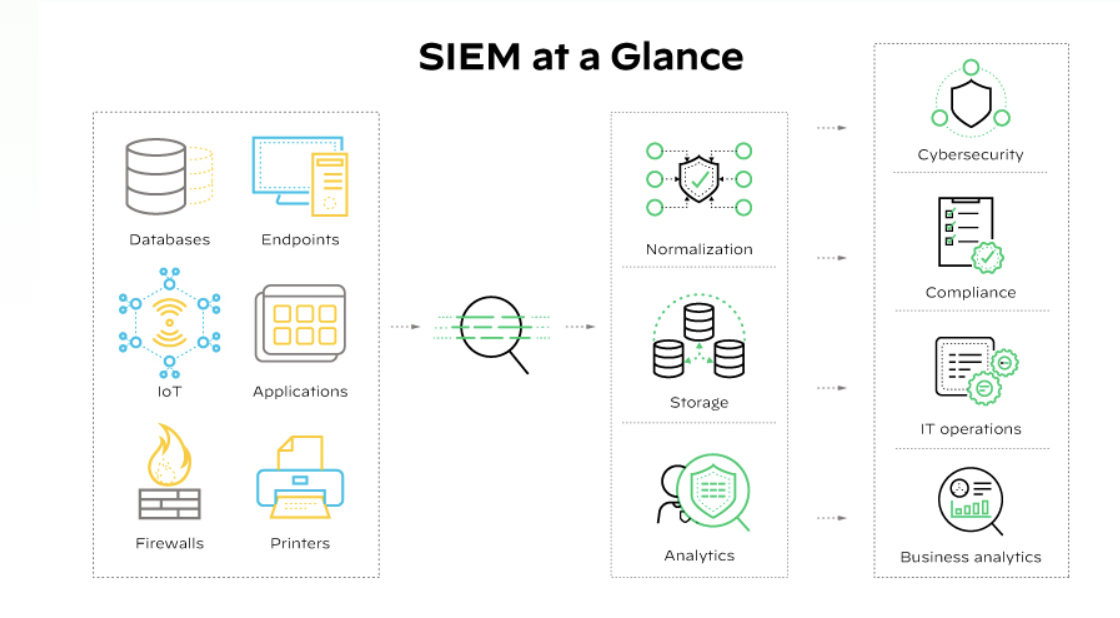
SIEM (Security Information and Event Management) software collects and analyzes security data from an organization’s IT environment to detect, investigate, and respond to threats. The following are the steps, summarized:
- Data Collection – SIEM gathers log and event data from various sources like firewalls, servers, endpoints, and applications.
- Normalization – It standardizes the data into a common format so it can be analyzed uniformly.
- Correlation & Analysis – SIEM software uses rules and machine learning to identify patterns and correlate events that may indicate a security incident.
- Alerting – When suspicious activity is detected, SIEM generates alerts for security teams to investigate.
- Dashboards & Reporting – Provides visualizations, reports, and real-time monitoring to help with compliance and situational awareness.
- Incident Response – Some SIEMs integrate with SOAR tools to automate responses like isolating endpoints or blocking IPs.
SIM vs. SEM vs. SIEM
Imagine SEM as a real-time alarm system, swiftly identifying threats as they happen. In contrast, security information management (SIM) is like a detailed record keeper, meticulously storing and analyzing historical data.
Together, they form a powerful duo, often integrated into security information and event management (SIEM) systems, providing a comprehensive overview of security health.
Understanding the distinctions between SIM, SEM, and SIEM is vital in the realm of cybersecurity. Their integration is essential for developing comprehensive security strategies. SEM and SIM are the two pillars of what is now known as SIEM, and these discrete approaches can be defined as follows:
- SIM systems collect and analyze log data, including network and system logs, for long-term storage and generate reports for compliance purposes.
- SEM enables the recording and evaluation of event data and helps security or system administrators to analyze, adjust, and manage the information security architecture, policies, and procedures. It provides immediate alerts when potential security incidents are detected, allowing security teams to react quickly. SEM also includes the ability to correlate different events from various sources, aiding in detecting complex cyberthreats.
- SIEM systems combine SIM and SEM capabilities to offer long-term storage and analysis of log data and real-time monitoring and response capabilities. By providing a comprehensive security overview, SIEM enables the detection of sophisticated threats that require real-time events and historical data analysis. They also have advanced features like UEBA, SOAR, and advanced threat intelligence integrations.
To contextualize these threads in today's parlance, it is essential to understand that SIEM tools have become a standard solution in the modern security operations center. Today's advanced SIEM platforms serve as the nerve center for both SEM and SIM, offering functionalities like log collection, normalization, correlation, and reporting as a contiguous whole rather than separate capabilities.
SIEM platforms now commonly leverage machine learning and artificial intelligence to enhance detection capabilities, allowing for more accurate identification of threats amidst vast volumes of data.
Security Event Management (SEM) FAQs
One of the pioneering commercial SEM applications was ArcSight ESM (Enterprise Security Manager), developed by ArcSight, which gained prominence in the early 2000s. ArcSight ESM was also one of the first comprehensive SIEM solutions available.
Such standalone offerings have been eclipsed in the marketplace by more advanced offerings such as Cortex XSIAM from Palo Alto Networks. They are incorporating out-of-the-box AI models, and advanced solutions such as Cortex XSIAM go far beyond traditional SEM detection methods, connecting events across various data sources to accurately detect and stop threats at scale. In this way, it becomes possible to automate security tasks to reduce manual work and accelerate incident response and remediation before analysts even look at incidents.