What Is IoT Security? Internet of Things Network Security
IoT security is the practice of protecting internet-connected devices and the systems they rely on from unauthorized access, misuse, and disruption.
It addresses vulnerabilities introduced by limited device controls, diverse connectivity methods, and inconsistent update mechanisms.
Strong IoT security helps prevent device compromise, data exposure, and lateral movement within connected environments.
Why is IoT security important?
IoT security is important because internet-connected devices interact with physical systems and digital networks in ways that create new opportunities. And new vulnerabilities.
These devices often operate with minimal controls. Yet they collect, transmit, and act on sensitive data in homes, businesses, and critical infrastructure.
Without purpose-built security, IoT systems can be exploited to steal information, disrupt operations, or serve as entry points into larger networks.
- 81% of security leaders say their organizations experienced an IoT-focused attack in the past year.
- Organizations hit by IoT-targeted breaches were significantly more likely to face costs between $5M–$10M than those hit by traditional IT attacks.
- 46% of organizations still struggle to gain visibility into their IoT devices, making risk management extremely difficult.
Not to mention, new use cases emerge faster than security models can adapt.
As artificial intelligence becomes more embedded in IoT ecosystems—enhancing threat detection, trust management, and device decision-making—it also introduces new attack surfaces that further raise the stakes for securing connected environments.
Plus, many devices remain deployed long after their support lifecycles end.
What are the primary IoT security risks and challenges?
IoT environments introduce risk in ways that traditional IT systems don't.
Many devices operate outside the reach of standard controls. They're physically exposed. They have limited compute resources. And they're often deployed without clear ownership or long-term support.
That's what makes IoT security difficult. It's not just about technology. It's about how these devices are built, deployed, and managed across environments that may not be built for oversight.
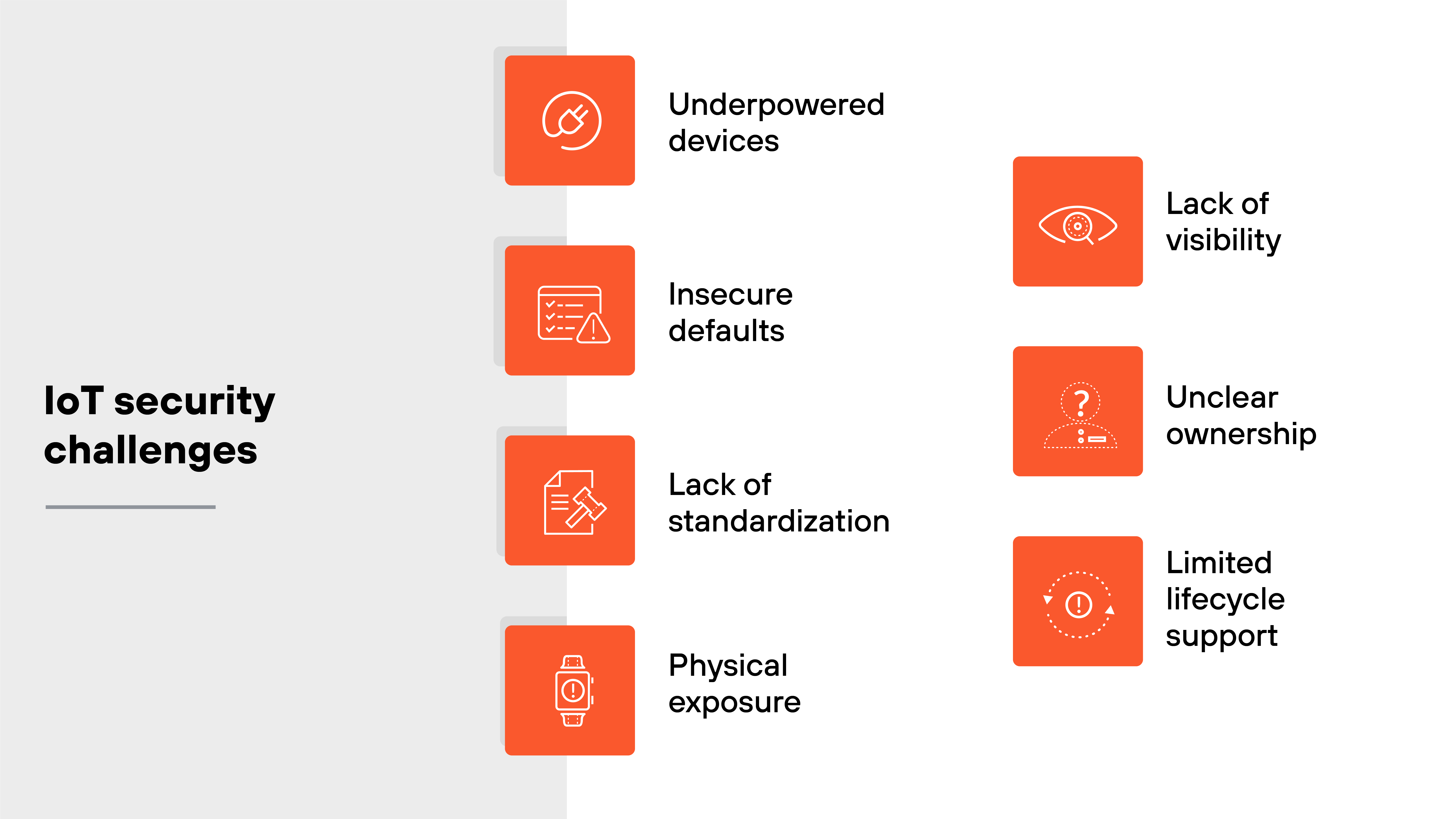
Here's where the biggest challenges show up:
Many IoT devices are underpowered. They lack the processing capacity to run traditional security software or encrypt traffic reliably.
And they often ship with weak defaults, insecure firmware, or hardcoded credentials that never get changed.
There's also no standardization. Devices come from different vendors, run different software, and use different communication protocols. That makes it hard to apply consistent policies or updates across a fleet.
- 91% of security leaders say IoT device manufacturers do a poor job securing devices from attack.
- Manufacturers are projected to increase their use of OT assets by 400% by 2030—most of which were not designed for secure internet connectivity.
And then there's the lifecycle problem. Devices stay in use long after their support ends. Or worse, with no support policy at all. Updates are rare. Patch management is nearly impossible. So vulnerabilities linger.
Physical risk matters too. Unlike IT assets locked in data centers, many IoT devices are deployed in the open. Think parking meters, industrial sensors, or consumer gadgets. If an attacker can get to the device, they may be able to bypass software protections entirely.
Visibility is another challenge. Many IoT devices are invisible to IT teams. They don't show up in inventory. They aren't monitored. And they may not even be known to security staff. Until something goes wrong.
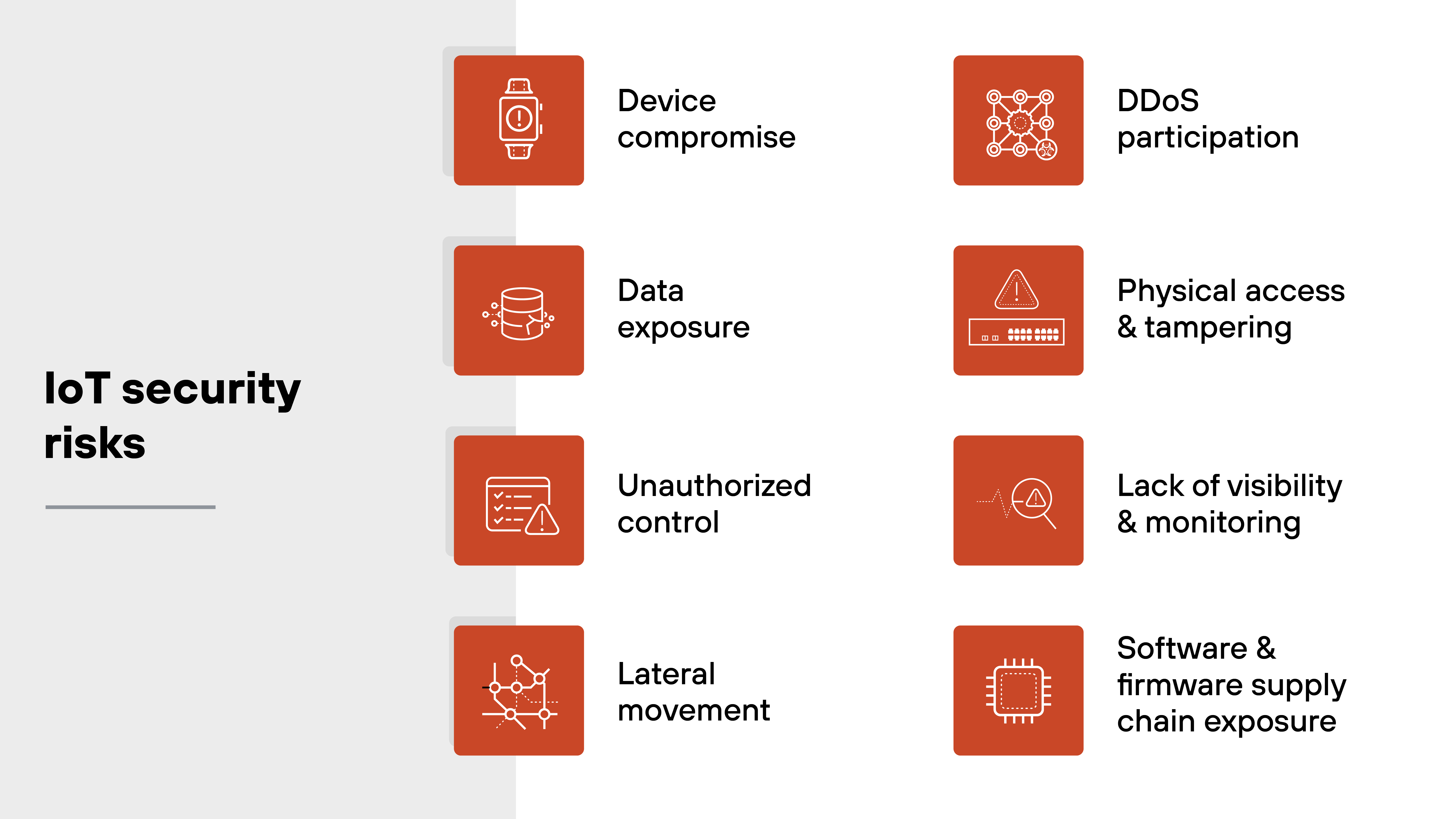
What happens when these gaps are exploited?
Devices get compromised and used as entry points into larger systems.
Sensitive data is exposed through unencrypted traffic or weak authentication.
- Attackers issue commands or take unauthorized control.
- Lateral movement enables deeper access across networks.
- Devices are hijacked into botnets and used in large-scale DDoS attacks.
- Supply chain issues introduce hidden vulnerabilities through third-party firmware or components.
Ultimately, securing IoT means addressing both the limitations of the devices and the realities of how they're deployed.
Which IoT devices and industries are most vulnerable?
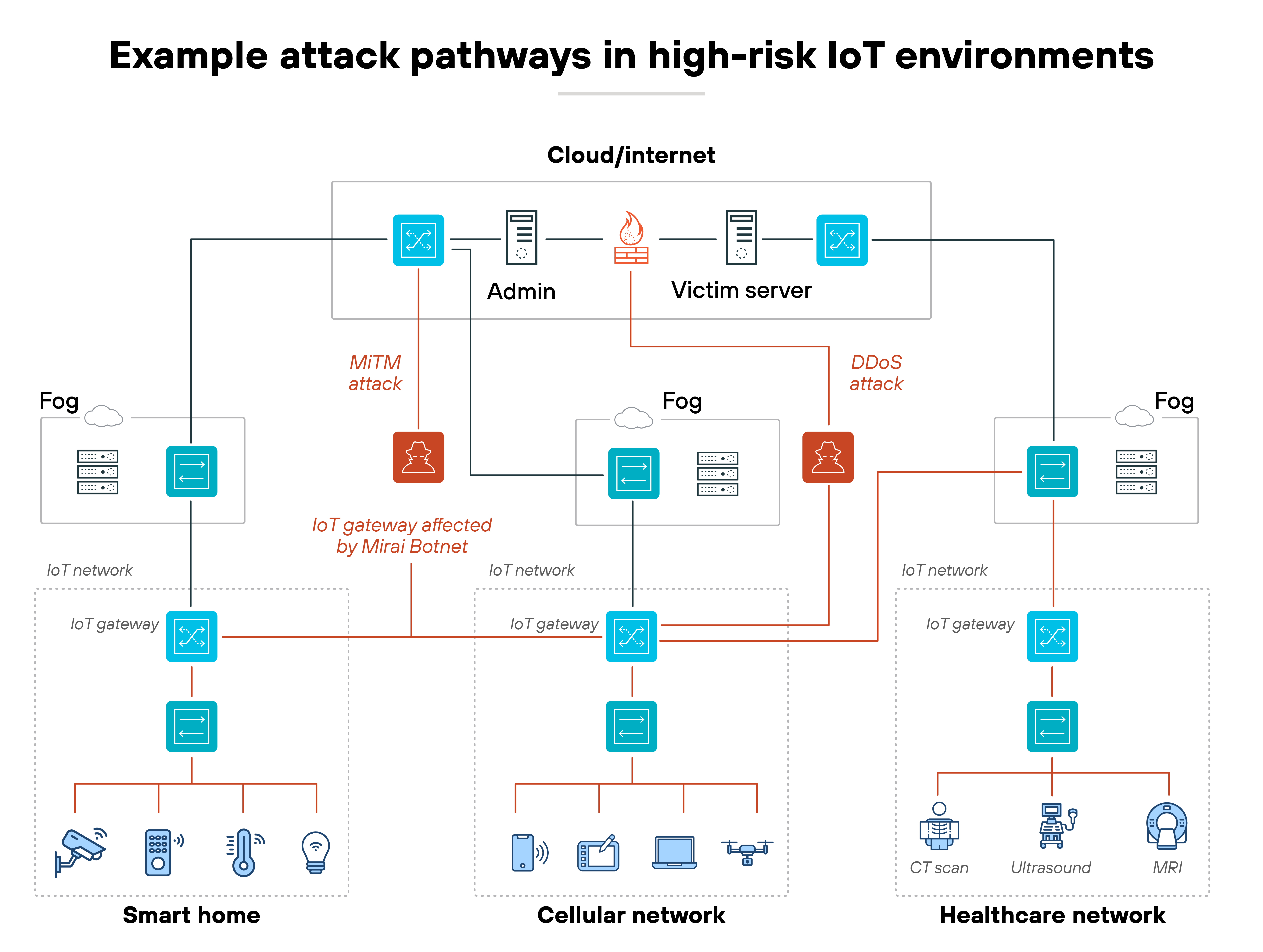
Not all IoT environments carry the same level of risk.
Some devices are inherently more vulnerable—because of how they're built, where they're deployed, or whether they can be updated and monitored.
And some industries rely more heavily on these devices in critical or distributed systems. Basically, the riskiest devices often show up in the riskiest places.
Here's a breakdown of high-risk device types and where they tend to appear.
| High-risk IoT devices and where they're commonly deployed | |||
|---|---|---|---|
| Device type | Example use | Why it's vulnerable | Common in |
| Consumer electronics | Smart TVs, voice assistants, doorbells | Weak defaults and rare security updates | Homes, retail environments |
| Home networking gear | Wi-Fi routers, range extenders | Often misconfigured or unmanaged by end users | Residential, small business |
| Security systems | Networked cameras, smart locks | Exposed to the internet and often lack strong authentication | Government, commercial, infrastructure |
| Healthcare devices | Monitors, wearables, infusion pumps | Handle sensitive data with limited ability to patch or monitor remotely | Hospitals, elder care, telehealth |
| Industrial control | Sensors, PLCs, automation units | Long lifespans and limited tamper protections | Manufacturing, utilities, energy |
| Connected vehicles | GPS trackers, infotainment systems | High mobility, long update cycles, and external network exposure | Transportation, logistics, consumer |
| Public infrastructure | Utility meters, traffic systems, surveillance | Distributed, physically accessible, and often lack IT-level asset management | Cities, municipalities, critical infrastructure |
| Retail / public kiosks | Smart vending machines, self-checkouts | Run on outdated platforms and are physically exposed | Retail, transit, quick-service locations |
How does IoT security work?
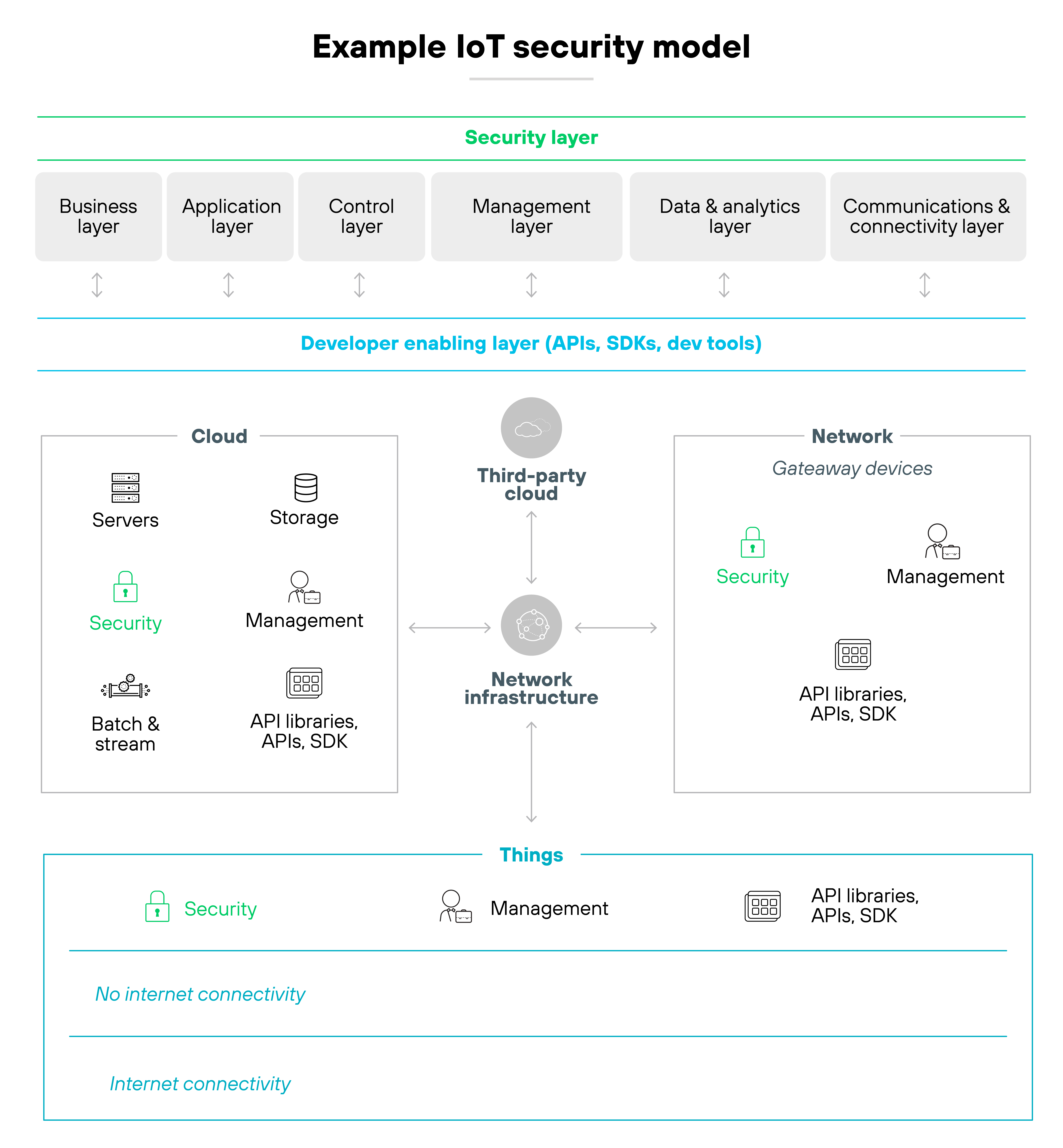
IoT security works by layering protections across the entire device lifecycle.
It starts with provisioning: assigning identities, applying secure configurations, and controlling initial access.
From there, protections like encryption, authenticated updates, and behavior monitoring help maintain trust. Devices enforce local policies, log key events, and report on their own posture when possible.
And if something goes wrong, recovery mechanisms help restore the device or safely remove it.
Because many IoT systems can't rely on constant updates or central control, strong security depends on designing devices and environments that can defend, detect, and recover on their own.
What are the essential elements of IoT security?
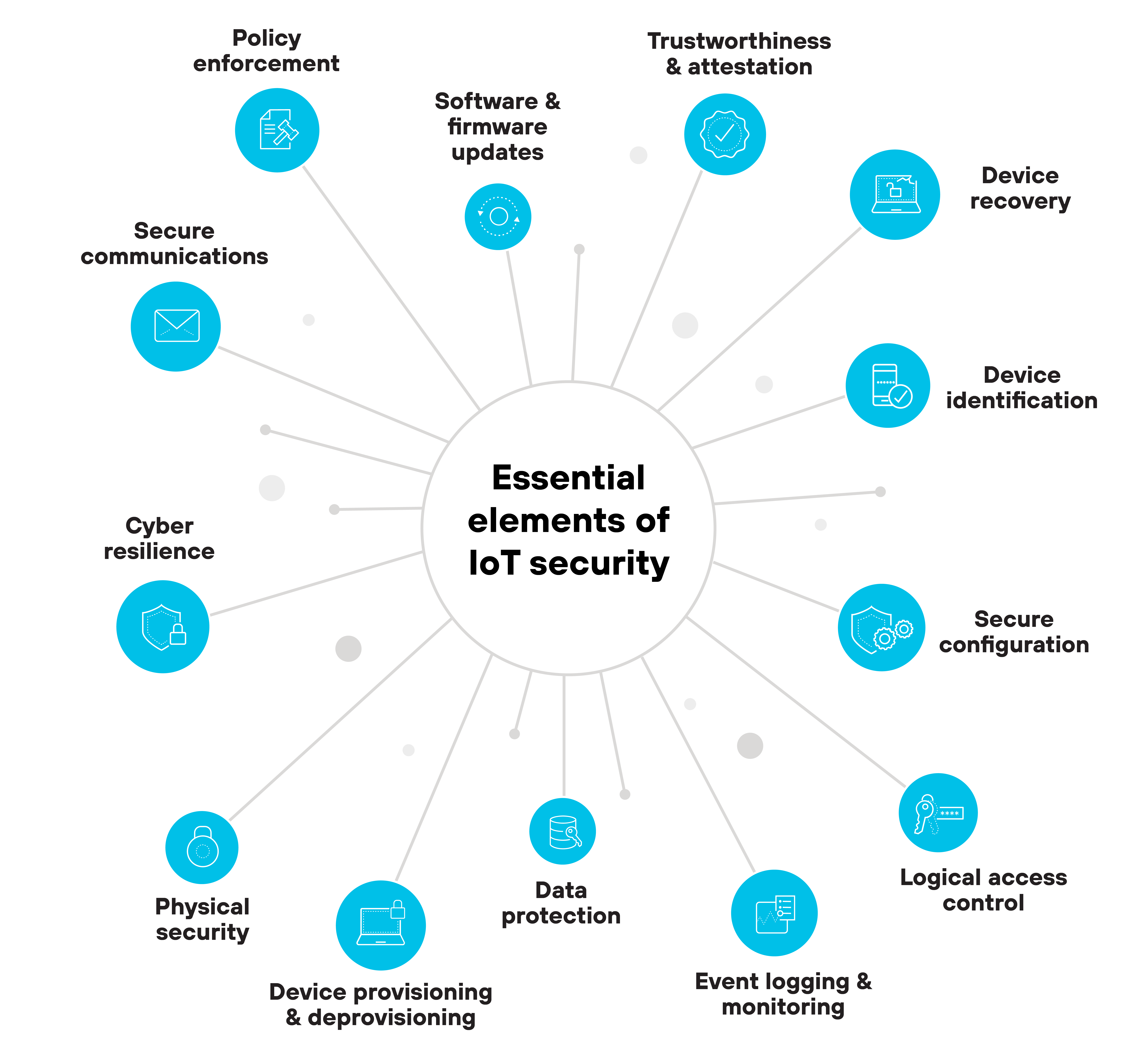
There's no single control that makes an IoT device secure.
Security depends on a combination of protections. Each focused on a different aspect of the device's lifecycle, functionality, and environment.
You need a full stack of coordinated elements that work together to defend against compromise, maintain operational integrity, and support secure management.
- Device identification: Each device should have unique logical and physical identifiers to support asset tracking, access control, and monitoring.
- Secure configuration: Devices must support authorized configuration changes and reject unauthorized ones. Secure defaults and restore points are important.
- Data protection: Confidentiality and integrity must be maintained for data at rest and in transit. Encryption and secure key management are essential.
- Logical access control: Only authorized users, services, or systems should be able to interact with the device. Role- or attribute-based policies help limit misuse.
- Software and firmware updates: Devices should accept only authenticated, integrity-checked updates. Signed firmware and code verification are critical.
- Event logging and monitoring: Security events like access attempts, config changes, and anomalies should be logged to support detection, investigation, and compliance.
- Device recovery: Compromised or malfunctioning devices should support restoration to a known-good state or allow for secure data wiping.
- Device provisioning and deprovisioning: Devices should support secure onboarding with identity validation and configuration enforcement. Deprovisioning should revoke access and erase data.
- Physical security: Devices in exposed locations should include tamper resistance and protections against key or firmware extraction.
- Cyber resilience: Devices should maintain safe operations under attack, including denial-of-service resistance and degraded-mode functionality.
- Secure communications: All network communications should be encrypted and authenticated. Devices must avoid transmitting sensitive data over insecure channels.
- Trustworthiness and attestation: Devices should be able to report on their own security posture, software state, and configuration integrity to support trust decisions.
- Policy enforcement: Devices should enforce local rules such as access limits, rate controls, or usage restrictions based on their role and conditions.
What frameworks, standards, and regulations guide IoT security?
Several frameworks and standards help guide how organizations approach IoT security.
Some apply broadly across devices and industries. Others are tailored to specific contexts—like consumer products or industrial systems.
Here's a quick overview of the most relevant ones:
| IoT security frameworks, standards, and regulations | |||
|---|---|---|---|
| Name | Type | Description | Applies to |
| NIST Cybersecurity Framework (CSF) | Framework | Provides voluntary, high-level guidance for managing cybersecurity risk. Often used as a foundation for other IoT-specific efforts. | All sectors |
| NIST SP 800-53 | Standard | Offers detailed security and privacy controls used by federal systems, adaptable to IoT environments. | Federal and critical infrastructure |
| NIST SP 800-82 | Standard | Focuses on securing industrial control systems, including IoT components used in OT networks. | Industrial / OT |
| NIST IR 8259 & 8259A | Baseline guidance | Defines the core baseline of capabilities IoT devices should support for cybersecurity readiness. | IoT device makers |
| NIST IR 8228 | Risk guidance | Offers recommendations for identifying and mitigating IoT-specific risks, including device lifecycle concerns. | General IoT use |
| ETSI EN 303 645 | Standard | Sets baseline security requirements for consumer IoT devices. Emphasizes outcome-focused controls like password policies and secure updates. | Consumer IoT |
| IoTSF Compliance Framework | Framework | Developed by the IoT Security Foundation to support secure-by-design practices across the device lifecycle. | Commercial and industrial |
| Industrial Internet Security Framework (IISF) | Framework | Developed by the IIC, focused on securing the Industrial Internet of Things. Emphasizes trustworthiness and secure data flow. | IIoT / industrial |
| PSA Certified | Certification | Hardware-based certification scheme backed by Arm and industry partners, aligned to threat models and best practices. | Embedded IoT |
| IoT Security & Privacy Trust Framework (OTA) | Framework | Outlines principles and recommendations for trustworthy consumer IoT products. Focuses on privacy, updates, and disclosures. | Consumer-focused |
Learn how to unify OT and IT security without compromising productivity, featuring A CISO's Guide to Navigating OT & IT Convergence in the Manufacturing Industry.
Download eBookIoT security FAQs
- Device security – focuses on protecting the device itself (firmware, access control, physical hardening).
- Network security – ensures secure communication and prevents unauthorized access or data interception.
- Operational security – covers monitoring, updates, lifecycle management, and response to threats across the IoT ecosystem.
- Visibility – knowing what devices are on your network.
- Control – enforcing configuration, access, and communication policies.
- Protection – applying encryption, authentication, and segmentation.
- Resilience – ensuring systems can detect, respond, and recover from compromise.